Getting files out of a running VM in Hyper-V 2012 remotely
I was reading the post by Ben Virtual-PC Guy about how to get files out of a running virtual machine.
I have altered his bits to work also when not running on a Hyper-V host (as Mount-VHD does not work when not Hyper-V is enabled), and you have the VM´s on a smb share, this also works if you take a snapshot and then copy the vhdx file to a windows 8 or windows 2012 machine.
The cool part is that I can use a UNC share path with Mount-DiskImage which is the Cmdlet used.
If I have the right permissions I can then easily with just a PowerShell script as Ben showed mount the virtual harddisk and copy the files, and this from a remote server and not on the Hyper-V host.
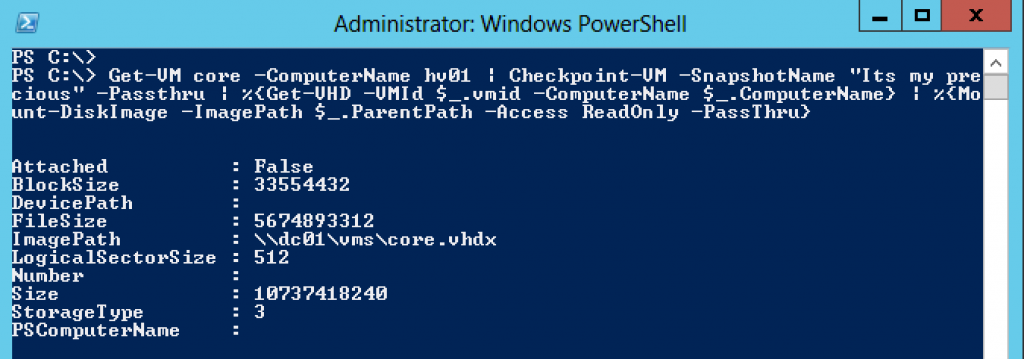
Get-VM core -ComputerName hv01 | Checkpoint-VM -SnapshotName "Need to look at these disks" -Passthru | %{Get-VHD -VMId $_.vmid -ComputerName $_.ComputerName} | %{Mount-DiskImage -ImagePath $_.ParentPath -Access ReadOnly -PassThru}
After I have run this you see that I can then get the secret file out of the running virtual machine
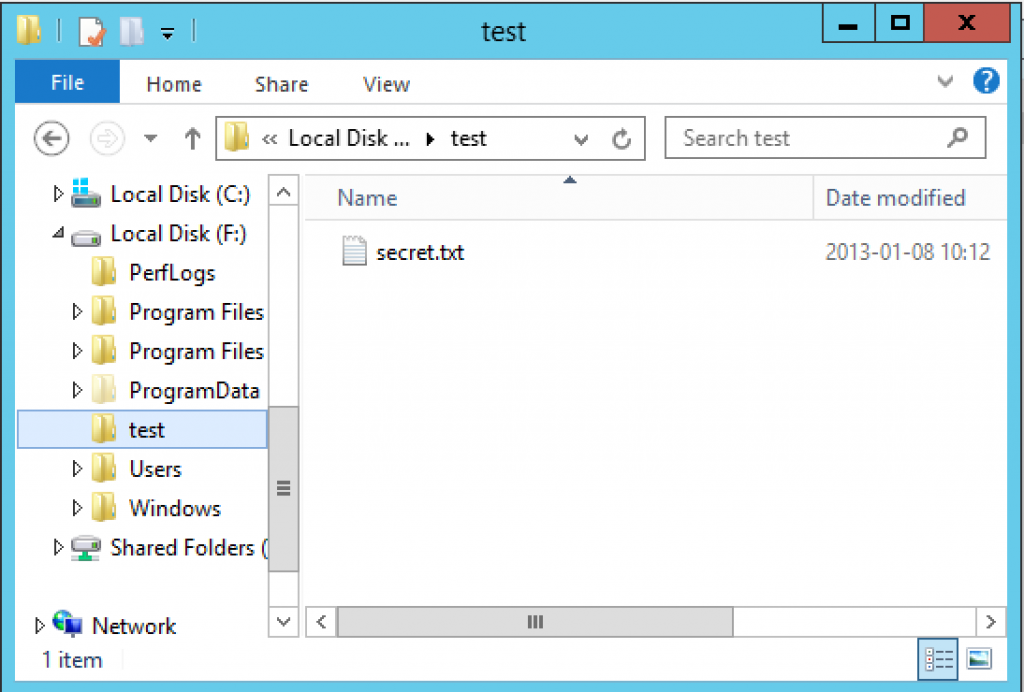
and when I am finished copying the secret files from the running virtual machine I can unmount the disk and remove the snapshot.
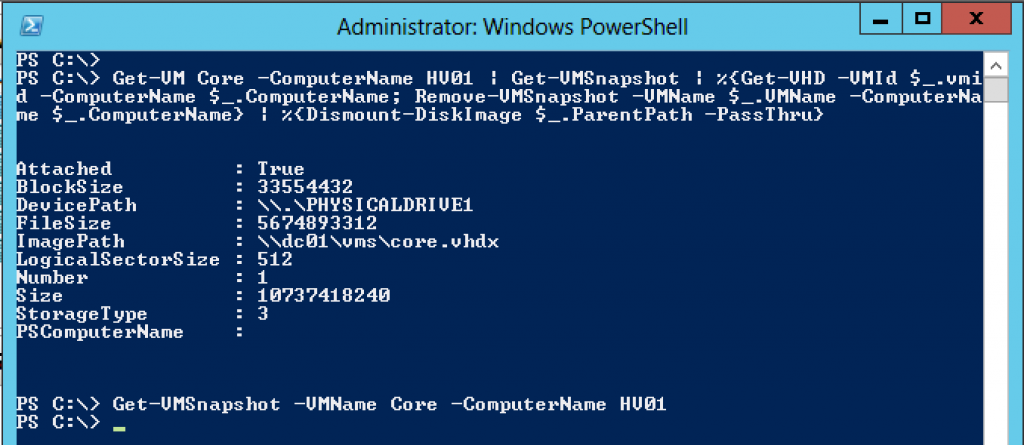
PS C:\> Get-VM Core -ComputerName HV01 | Get-VMSnapshot | %{Get-VHD -VMId $_.vmid -ComputerName $_.ComputerName; Remove-VMSnapshot -VMName $_.VMName -ComputerName $_.ComputerName} | %{Dismount-DiskImage $_.ParentPath -PassThru}
So what is the conclusion on this in a security perspective, as you can see it is quite easy for a person with the right permissions on a host level to get access of files that he or she maybe not should see. Talented hackers can get permissions and accounts that they need. This leads to the discussion of course where you should put your hosts, is it enough security and boundaries on your network and in your Active Directory Domain or should you set up another for the Hyper-V hosts and management servers?!
Comments
[…] Ben the Virtual PC Guy did a blog post a while ago where he showed how to get files out of a running machine, and I made a follow up where using a non Hyper-V host to get the files. […]
[…] And with this command I move a file into the VM, the parameter -FileSource that only accepts Host today implies that it might be possible to also move files from the VM to the host in a later version. (this can be done with the mounting of the parent disk of a vhd/vhdx after a snapshot that I have don…) […]