AWS Cloudwatch – watch out for outdated EC2config
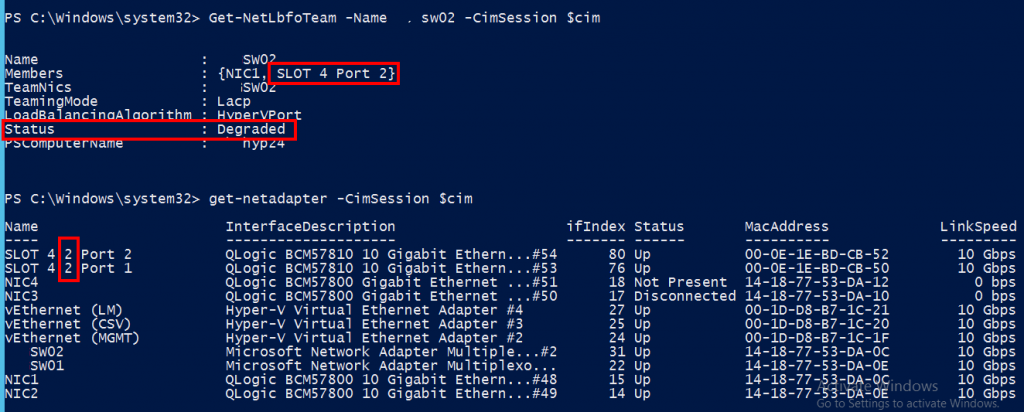
I configured a Windows instance on AWS to start reporting logs and performance counters into their AWS Cloudwatch for centralised overview.
The day after I had started monitoring I found that it was consuming loads of CPU and memory and thus not normal,
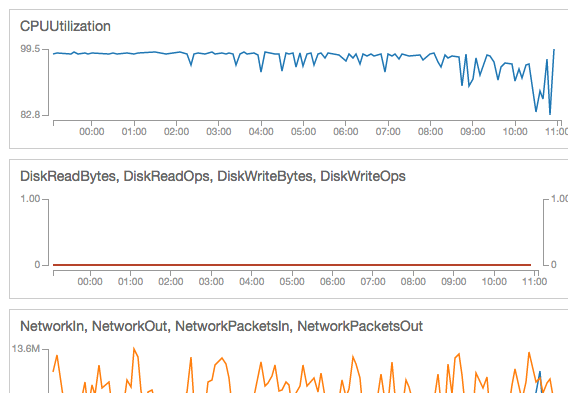
Going into the instance, which took a while as it was so sluggish, I found that the EC2Config service was going berserk and I had to kill it.
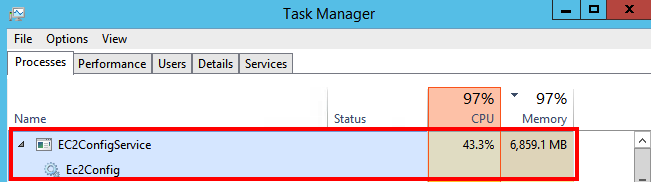
Looking at the properties of the EC2 you can see that it was 2.2.12.30 and far from the version available today.
So if you want to enable Cloudwatch make sure that you first update the EC2config to be sure that your server will survive the burden of monitoring ?