Recover Administrator password after some powershell on the Active Directory
Yes powershell can be used to administer your Active Directory, but you could do some serious damage also. I will show you one particular case where things can go very wrong and how to recover from it.
To use cmdlets for AD you simply start your powershell console and type
Import-Module ActiveDirectory
You get quite a few cmdlets to help you automate your user administration, if you write the following in your console it will list all of them.
Get-Command *-AD*
Well now to the problem, as a domain admin you do have some privileges and say that you want to disable some user accounts and you forget to add a searchbase or your filter does not do as you wish and in one line you have disabled all accounts in your domain, including admin. IF and i say IF you realize that misstake and quickly go in and enable the accounts again, you are safe, but if you log out of your session you wont be able to log in again with any account 🙂
Get-ADUser -Filter * | Set-ADUser -Enabled $False
try to log in as domain administrator and you will get this, on any DC (as long as your replication is working and if it is not you have other problems, trust me)
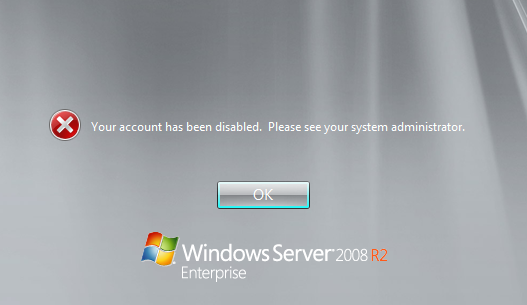
So how do we fix this then? luckily there is a way to do this and it is quite easy. You have to find a windows iso and as in this case a Win 2008 r2, start it in repair mode and start a CMD
when the command promt is started do this (i found it in another blog from Matheu the difference here is that i use net user administrator /active:yes to enable instead of change password)
- Go to c:\windows\system32
- Rename Utilman.exe to Utilman.exe.bak
- Copy cmd.exe to Utilman.exe
- Reboot on Windows
- Do the keyboard shortcut Windows + U when on the logon screen
- net user administrator /active:yes
- log on with the domain admin account
- Reboot on the DVD to put back the original Utilman.exe
Instead of panicking and try to restore your AD you can easily as i described log in again. This is of course a big security thing to consider in a virtual environment where users that have access to the virtual infrastructure but are not domain admins can manipulate virtual Domain controllers to get access to the administrator password “net user Administrator newpasswd123”. Here is a link to all net user commands.
So if i am going to do some account disabling i would include a searchbase in my Get-ADUser to not get the Administrator locked out by mistake and actually take the right OU to modify users on.
Get-ADUser -Filter * -SearchBase "OU=Employees, DC=Test, DC=local" | Set-ADUser -Enabled $False
In my test environment i used two DC´s and both the lock and unlocking replicated quite fast. There is maybe a way with the Active Directory Domain Services Recovery without having to do a restore, i will look into that and do a follow up post if i find any easy ways!
Comments
[…] script with a menu to enable or disable accounts in the different OU´s. As i described in a earlier post it is quite powerful to use Active Directory cmdlets and i have tried to take care of that by […]
[…] I showed the attendes some nice ways to deploy your virtualization environment, and I also showed how to get yourself locked out in the Active Directory and getting back in, my post done with win server 2008 r2 is still valid for the win 2012 […]